Password Encryption
Password encryption is essential to store user credentials securely. Without password encryption, anyone accessing the configuration files for aqishare could easily view any stored passwords by default, because it is stored as plain text. To avoid this potential security risk, it is possible to encrypt all passwords in the configuration files with an encryptor tool. The tool uses the asymmetric RSA algorithm to encrypt the passwords.
Download the Encryptor Tool
The password encryption tool is available for various platforms such as Windows, Linux and Mac. The package contains the executables for each of the mentioned platforms and can be downloaded from the delivery portal.
Download the password encryption tool, called aqicrpyt, from: https://aqipro.com/downloads/aqicrypt.zip. The package has a file size of approximately 6.5 MB and contains all executables for the mentioned platforms.
Once downloaded, extract the package. Depending on your current system architecture, you may also need to unzip either the .zip or .tar.gz archives to find the appropriate executable.
Using the Encryptor Tool
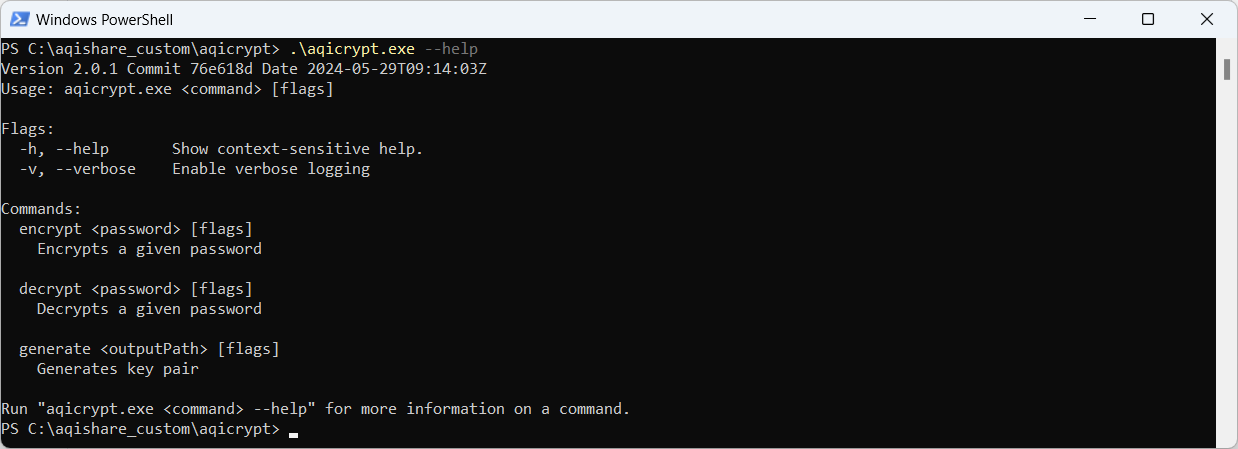
To encrypt passwords in any of the aqishare configuration files, follow the steps below. This guide demonstrates usage on a Windows system. If your platform is Unix or Mac, use the corresponding commands.
.\aqicrypt.exe --help
Generate Key Pair
Use the generate command to generate a new key pair. Pass the output path as an argument specifying where the private key and public key files should be stored. Ensure the specified directory exists.
.\aqicrypt.exe generate c:\aqishare_custom\keypair
Encrypt Passwords
Use the encrypt command to create encrypted passwords. Accepted arguments are the password to be encrypted and the public key file used for encryption.
.\aqicrypt.exe encrypt MY_PASSWORD_TO_ENCRYPT --publicKeyPath c:\aqishare_custom\keypair\publicKey.pem
The output will be like:
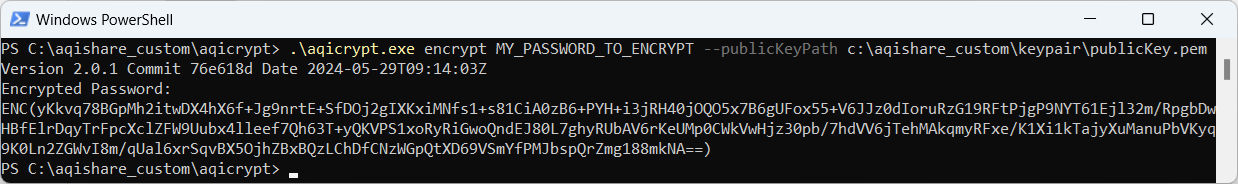
Copy the line starting with the ENC() function and use this as the value for the desired password instead of its plain text value.
You can use encrypted passwords in many of the aqishare configuration files. Refer to the Initial Setup chapter.
Decrypt Passwords
Use the decrypt command to decrypt an encrypted password. This command is for testing purposes only and has no relevance to the application. Use it to verify the encrypted passwords. This might help if there are issues in the running application that lead to incorrect passwords or passwords encrypted with a different key pair. It could also help if the password is no longer known.
Accepted arguments are the encrypted password string and the private key file.
.\aqicrypt.exe decrypt "ENC(yKkvq78BGpMh2itwDX4hX6spQrZmg188mkNA==)" --privateKeyPath c:\aqishare_custom\keypair\privateKey.pem
To execute the decrypt command successfully, please enclose the encrypted password in double quotes (i.e., "ENC(...)"). Alternatively, use the value inside the brackets without "ENC()".
The output will look as follows and display the decrypted password.

Enable Usage
Once the key pair is created and the passwords are encrypted and stored in the related configuration files, the following steps are necessary to enable the usage of the encrypted passwords in aqishare.
Map Private Key into Container
To allow the usage of the encrypted passwords based on the created key pair above, the private key file must be mapped into the aqishare container. Depending on the containerization tool used, the method to make files available may vary (either map it or copy it).
Refer to related section in the Application Start to learn how to map it correctly.
Specify Private Key
Once the private key file is available inside the container, aqishare must be made aware of it to use it. To accomplish this, add the path of the private key file within the container to app.yaml.
privateKeyPath: /app/configs/privateKey.pem
Refer to related section Password Encryption in the app.yaml.